How Cloud-delivered Security Can Meet The Needs of Today’s Workforce
The remote workforce is here to stay. Thanks to global shifts in working standards as a result of both evolving technology and the COVID-19 pandemic, increasing waves of people are working from home. Many, too, are working to a hybrid workforce model – with secure access to platforms and data from afar, but occasionally working in-house.
In any case, as the shift to remote working has grown, security gaps have emerged. It is all well and good to have secure web gateways and a firm security posture in-house – but what happens when your team is working in the field? How does the user experience change – can you be sure that they, and the data they are handling, is fully protected outside of your physical oversight?
Remote users and mobile users, while still working under your enterprise umbrella, will demand a network architecture that protects them out in the open. If you can’t be sure that you trust network access from afar, regardless of the user logins and permissions you have in place, it may be time to talk to a reliable cloud access security broker.
But how exactly can a cloud service help in terms of remote security – and how easy is it to set up?
What is Cloud Security?
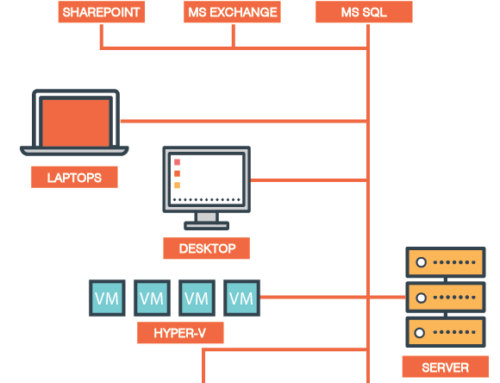
Cloud delivered security works much in the same way you’d expect cloud storage or cloud server support to. With public clouds, for example, users can store data such as documents and retrieve them from any data-connected device using the same login credentials.
Security threats that affect physical data storage do not have the same impact on cloud data. Security solutions in the cloud can centralise to affect multiple applications and resources, and what’s more, users and businesses connecting to the cloud will not need to manage security strategies on their own steam.
Much like cloud storage and server access, security controls through the cloud are maintained and tweaked off-site, meaning that users can essentially log in with greater peace of mind. This means, too, that remote users can access all the security capabilities of an in-house model without having to worry about being tethered to the office.
Why Might I Need Cloud Security Protection?
Security risks are always evolving, and when it comes to moving a workforce to a remote or hybrid model, there is a need for a completely different approach to security. After all, it is not possible to rely on all users outside of the office to stick to the same antivirus and firewall protection. Cloud- based security effectively ensures all remote users and workers can access the same apps and
data from a singular platform, and at the time, receive protection from the same security standards.
Legacy networks operating purely in-house, of course, can also stand to benefit from cloud security. Network complexity – particularly when it comes to security measures – can throw many business managers and everyday users off. Managing network functionality in-house will take time and
dedication to understand, let alone to manage, upgrade and monitor over time.
Therefore, in the modern age – the healthiest approach to protection lies firmly in the cloud. While it is understandable that some traditional ofice managers may not wish to move all data into the cloud immediately, the benefits of a ‘floating’ service are widely documented – not only from an ease of backup and disaster recovery standpoint, but also from that of consistent protection against cyberattacks, malicious code and unwanted intrusion.
If you are working more and more towards a mobile workforce model in the months and years to come, then it is high time you considered making your security mobile, too. Poor user experiences in the field are, by and large, caused by a lack of understanding and connectivity with HQ – with the cloud, you can provide safe access for users no matter where they are based, ensuring that everyone is working from the same page.
What are the Further Benefits of Cloud Computing?
Cloud computing, not merely cloud security on its own, holds a raft of immense benefits for enterprise users across the board. Transferring storage and backup maintenance to a cloud platform, for example, will immediately reduce pressure and lower costs in-house. As mentioned, applying the same cloud security standards to each user location in the field is simple to achieve providing you partner with a leading developer in cloud solutions.
Broad protection aside, cloud-based applications are more reliable in the long-term. Not only does application performance improve through tailored security standards, remote users are more likely to expect reliable access to applications on the go. The nature of the cloud means that you are not relying on any one single server. IT-sanctioned applications available in the cloud operate through multiple disparate servers, and a leading cloud service provider will ensure your business – and your applications – continue running in the event of minor downtime.
Do also consider the fact that any application line-up hosted in the cloud is infinitely scalable. It’s entirely possible to change the apps and programs you work with from day to day. Therefore, if your business is undergoing serious growth, you can depend on the cloud to scale back or evolve with you as you demand.
Can I Use Cloud Security on Any Device?
Secure private access is entirely possible across a variety of different devices. Hybrid cloud environments, for example, will allow users to access both sensitive and shared data through mobile devices as well as standard PCs and laptops.
The cloud environment you build is as flexible as you need it to be. When it comes to effective
digital business transformation, moving your remote workforce to a secure cloud standard is one of the best moves you can make.
Whether you need greater protection against DDoS attacks, or simply need to offer remote users access to business documents on the move, we’re here to help you set up a bespoke solution in the cloud that grows with you – and never against you! Make cloud access and connection part of your internet security policy with immediate effect.