Office 365 – Attack Simulation Training

Microsoft has recently revamped their Microsoft 365 Defender product and it now has an interesting new section called “Attack Simulation Training” which gives admins the ability to run realistic attack scenarios against users in their own organisations.
These simulated attacks can help identify users who may be vulnerable to a real phishing attempt and prompt them to run through some basic email safety training to increase their awareness of potential attacks and hopefully decrease the risk of data loss or credential leaks.
The first step for running a simulated attack is to select the technique you want to use. Attack Simulation Training uses different techniques, taken from the MITRE ATT&CK® framework:
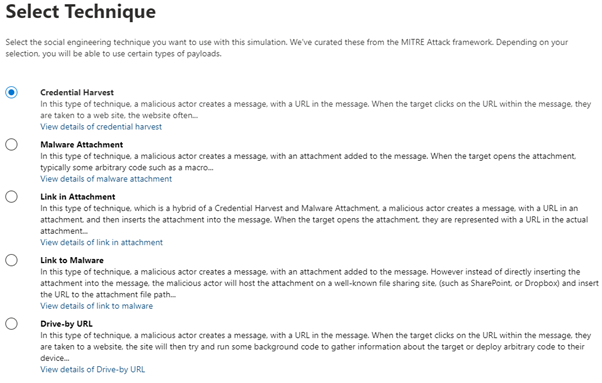
Once you have selected one of the techniques the next step is to name your simulation and then select a Payload:

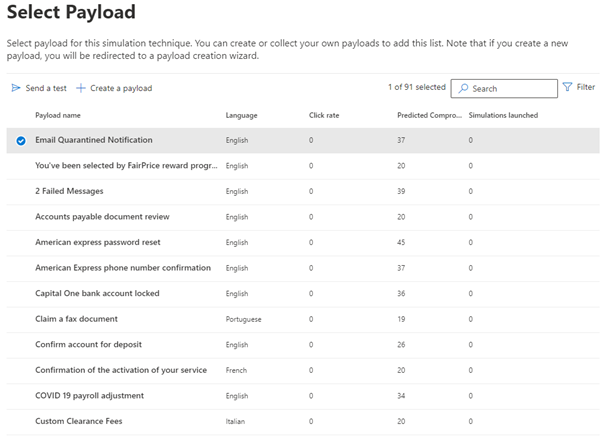
As you can see there are a lot of built-in payloads for you to choose from which are all designed to trick users into clicking. You can see the predicted compromise percentage rate for the different payloads and how many simulations have already been launched using each one.
In my example I’m going with the “Email Quarantined Notification” payload which has a 37% predicted compromise rate.
The next step is to select the users you want to target with the simulation. As I am only testing, I have just selected 1 user, but you can easily apply this to a whole company by selecting “Include all users in my organisation”
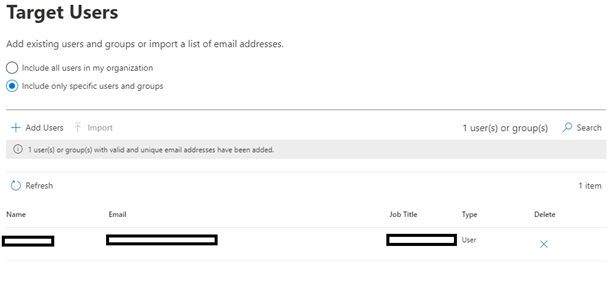
Once we have our targets added the next step is to select the options for assigning training to any unsuspecting users who click on the links and test malware files we will be sending them. This is not mandatory – you can specify no training as a preference or even redirect users to your own custom URL.
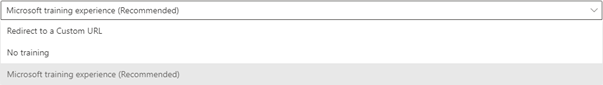
If you are specifying the Microsoft training experience, you then get 2 further options. The first is to allow Microsoft to assign the training for you (recommended) which it does based on a user’s previous simulation results and whether they have already been through any of the training programmes. You can also select specific training courses and modules yourself from Microsoft’s catalogue.
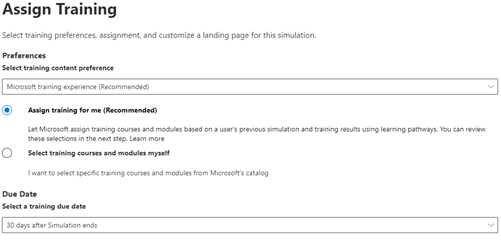
You must then specify the “due date” for any training the users require – the default for this is 30 days from when the simulation ends.
The next page allows you to set landing pages for any links users may click on. In this example we are using the default Microsoft landing page, but you can redirect to a custom URL or even create your own landing page in Office 365. The same screen allows you to add your own branding and logos to the emails and also gives the option to add payload indicators which can help users learn how to identify phishing emails.
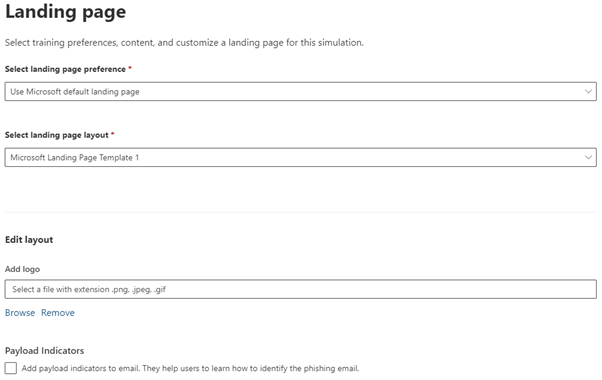
Once you are happy with the settings you can preview the landing page that users will see if they click on any of your simulated attack messages
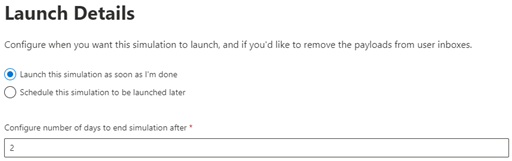
We’re almost ready to launch our attack simulation!
You can set it to be launched immediately or schedule a date for the first messages to be sent. You then set the length of time in days you want the simulation to run for. In my example I’m only going for 2 days but you can have these sent out over multiple days or even months.
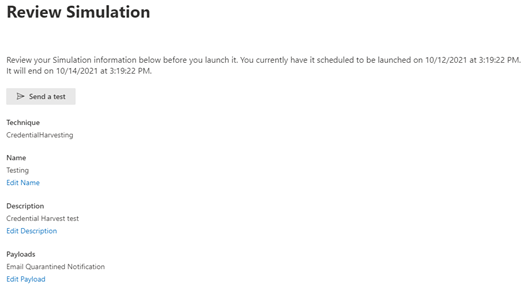
Once you have scheduled the launch date there is a final review where you can send a test message to yourself to check the formatting all looks ok.
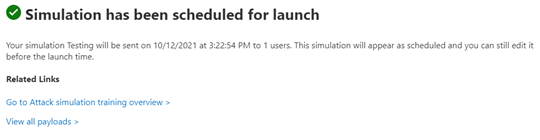
Once you have verified everything look OK you are ready to submit the simulation and your phishing messages will start being sent!
You can see an example of the phishing email which was sent to our test user below:
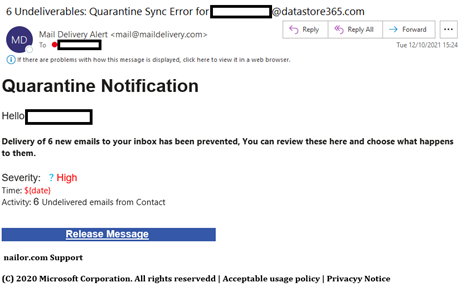
Once your attack has begun you will start to see updated information on the simulation showing how many emails have been delivered, how many users have clicked on the message, and how many have provided credentials.
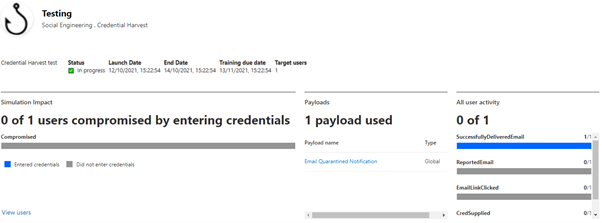
Attack Simulation Training can be a very powerful tool for admins to try and educate their users on how phishing works and some of the main indicators they need to look out for to prevent them falling victim to a real attack.
For more information on how you can protect your Office 365/Azure tenant drop us an email to info@datastore365.com and we will be happy to assist.
You can also check out some of the other services we provide here: https://www.datastore365.co.uk/services/
- Office 365 Backup
- Email Filtering
- Hosted private or public/hybrid cloud solutions
- Disaster Recovery As-a-service (DRaaS)
- Consultancy & Support Services